Information Technology
The API Security Disconnect
API security concern rises in manufacturing, energy & utilities due to legacy systems. Lack of visibility leads to vulnerabilities.
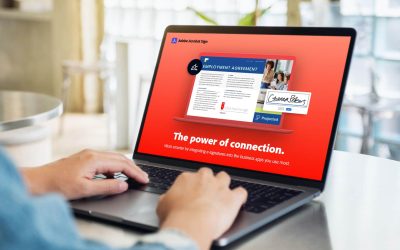
The Power of Connection
Acrobat Sign Solutions streamline workflows, save time, and enhance security. Radial saved $145,000 yearly integrating with Workday.
The Role of Video: Insights for Brands and Retailers
Video builds trust, connects with audiences, and boosts sales. Marketers prioritize video content for maximum engagement and ROI.
The Future of AI-Powered Contact Centers
IoT expands rapidly, set to reach 75 billion devices by 2025. UTIMACO’s u.trust Identify ensures secure identity management in connected environments.
Buyer’s Guide For Graph Databases
TigerGraph outperforms competitors like Neo4j and Amazon Neptune. Customers value its integration ease, flexibility, and high-speed analysis.
TigerGraph and the Rise and the Future of Graph Database
TigerGraph excels in the graph market, offering superior performance, scalability, and enterprise features. Its GSQL efficiently tackles business challenges for Fortune 500 companies.
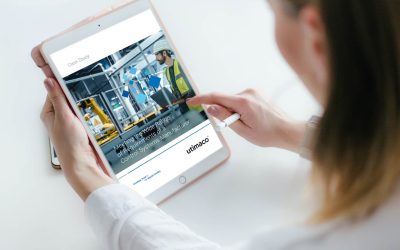
Meeting the Wide Range of Requirements of a Control Systems Manufacturer
UTIMACO delivered cybersecurity for a Control Systems Manufacturer, ensuring key management, tokenization, encryption, and compliance.
Secure SD-Branch Facilitates Technology Modernization for Australian Equipment Rental Business
Kennards Hire in Australia upgraded with Fortinet’s Secure SD-Branch, enhancing network performance and reliability.
Data Protection for Organizations
Data protection is critical. Encrypt sensitive information, control access, separate data and keys, monitor transfers, limit admin access for security.
Old but Gold Why Public Key Infrastructures are the security enabler for connected environments across all industries
Underestimating cyber risks leaves companies unprepared. UTIMACO’s u.trust Identify provides a comprehensive PKI solution for secure communication.
Enabling Strong Security for Your Connected Production Environment
IoT expands rapidly, set to reach 75 billion devices by 2025. UTIMACO’s u.trust Identify ensures secure identity management in connected environments.
4 Steps to Achieving Comprehensive Kubernetes Security
Crucial Kubernetes security guide: focus on development, images, connections, runtime. Use Policy as Code, Terrascan, Security as Code for robust measures.