Information Technology
Maximize your Microsoft Investment: Single-Solution Data Protection for the Microsoft Cloud
Metallic secures your Microsoft Cloud data! Extended backups, fast restores, and isolated copies keep it safe. Multi-layered security, ransomware defense, and one-view management give you complete control.
Metallic® DMaaS Shared Responsibility Model
Metallic DMaaS shares responsibility: Metallic handles infrastructure, security, and compliance. You manage backups, plans, and monitoring. They ensure data protection and service, you manage backup tasks and track usage for optimal data control.
Critical Deception Use Cases
Metallic shields your “crown jewels” with ThreatWise™. Deceptive tactics prioritize your most valuable data (CJA) for high-alert protection against ransomware and malware. for a tighter cyber defense.
Modern Data Protection Success Stories
Metallic ThreatWise™ stops ransomware cold with early warnings. Decoy tech fools attackers, protects data. Industry-proven and adaptable, it catches zero-day threats before they strike.
Cyber Risk Commands the C-suite’s
Collab tools worry 75% of firms as email threats surge (82% see higher volume, 76% fear big damage). Human error in 95% of breaches! Train staff, secure data!
Best practices in cloud-based backup
Metallic simplifies data protection for hybrid clouds. Easy backups, fast restores, and eDiscovery for legal compliance keep your data secure and accessible across any storage or cloud setup.
Multinational life insurance company enhances CX powered by Uniphore’s U-Self Serve™
Life insurer boosts CX with Uniphore’s U-Self Serve™. AI virtual assistant empowers customers (self-service, FAQs), improves sales, and automates tasks. Perfect for high-value clients, it tackles self-service gaps for better engagement.
NVIDIA NeMo Megatron on NVIDIA DGX Systems
NeMo Megatron on NVIDIA DGX cuts through LLM complexity. Businesses can build custom NLP tools for better customer experiences. Optimised hardware and software speed up training and scaling, making AI projects efficient and affordable.
How to Reduce the Risk of Phishing and Ransomware
Rising ransomware hits! Cloud defenses, employee training, and multi-factor auth with biometrics are critical. Educate staff to spot phishing scams. Be cyber ready!
Guide for the new normal way of working
New normal, new needs! Businesses prioritize network security, upgrade comms, and embrace cloud solutions like Rainbow for the rise of hybrid work (56% planning). ALE keeps teams connected for seamless business continuity.
NVIDIA H100 Tensor Core GPU Architecture EXCEPTIONAL PERFORMANCE, SCALABILITY, AND SECURITY FOR THE DATA CENTER
Nvidia’s H100 GPU boasts major performance gains over A100. Tensor Memory Accelerator speeds data flow, while Confidential Computing secures information. New DPX instructions tackle genomics, and 4th-gen NVLink boosts communication.
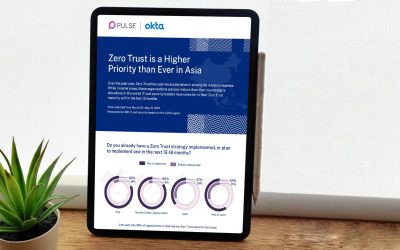
Zero Trust is a Higher Priority than Ever in Asia
Across Asia, 82% of companies are embracing Zero Trust security, with rising budgets to fortify networks and user access. Despite talent gaps and cost hurdles, Asia stands out in biometrics and SMS security, prioritizing integration with SIEM systems.